Features and Functions of Firewalls
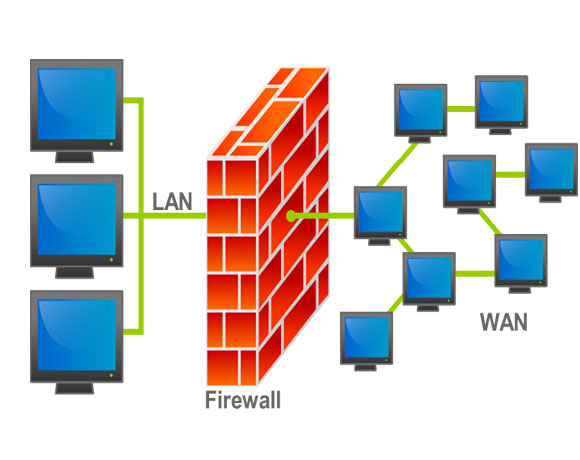
A firewall is a protective barrier between your PC and cyber world. When you are connected to the Internet, you are a potential target to an array of cyber threats, such as hackers, Trojans, and key loggers that attack through security holes. This means that if you shop or bank online, are vulnerable to identity theft and other security threats.
While using internet you are constantly sending and receiving packets of information. The firewall filters these packets and thereafter blocks or allows the data. This helps in preventing hackers to get inside and steal crucial data such as bank account numbers and passwords from you.

Basic firewalls such as the one in Microsoft Windows latest editions, only monitor incoming traffic by default. This may give you complete security, as outgoing traffic, like your credit card information, bank accounts, and passwords are not protected. An efficient firewall monitors both incoming and outgoing traffic. It also makes your PC invisible when you’re online, helping prevent attempted intrusions in the first place. Most firewalls are capable to continuously update the list of good and malicious applications. This way, your computer’s protection is always up-to-date.
You can categorize firewalls into two simple categories:
Hardware
A hardware firewall can be a router or any other security product that is placed between your PC and the outside world. More than one PC can be connected with that security device or router, and each will be protected by the firewall.
Proxy Server
Proxy server checks all messages entering and leaving the network and hides the true network addresses.
Packet Filter
Packet filter firewall checks each data packet entering or leaving the network. Packet filtering is fairly effective and transparent to users, but it is difficult to configure.
Software
A software firewall is installed on your PC, it will deflect incoming attacks and hide open ports. It will warn you about suspicious outgoing traffic. You can have a software firewall on each computer for strong protection. By installing software firewall, an attacker will have to cross two level security to access your PC.
Circuit-level Gateway
Circuit-level gateway is used for TCP or UDP connection. On establishment of secure TCP or UDP connection, data packets can flow between the hosts without further checking.
Application Gateway
Application Gateway security mechanisms is applied to specific applications, such as Telnet and FTP servers. It secures server effectively but slow down performance.
Next Generation Firewall (NGFW)
NGFW – next generation firewall is the newer class of firewalls that filters internet and network traffic based upon traffic types using specific ports. Next Generation Firewalls (NGFWs) feature the basic functionalities of a standard firewall with quality of service (QoS) in order to provide deeper and smarter inspection.
What is UTM (Unified Threat Management)
UTM is just another name for an all in one security appliance. A UTM appliance will consist of a firewall as well as other key security features such as spam filtering, web filtering, anti-virus, anti-spyware, anti-phishing, IPS/IDS, DOS and DDOS protection, Application filtering, Network Access Control, VPN’s and so on.
When the use of internet started rising and become an everyday need for many businesses and companies, so did the concerns for network security. This is when traditional firewalls and anti-virus packages became a mandatory need. As the years have rolled on, firewalls and anti-virus still very much at the heart of network and internet security have become just part of the solution. A firewall will filter on ports, protocols and connection states. If allowed, the traffic will filter through, and if denied the traffic is dropped. An anti-virus scanner will scan for viruses and either quarantine or delete if found.
However today there are many other advanced threats in which most are developed to fool firewalls and anti-virus filters. Therefore over the years as new advanced threats have emerged, so has the advanced techniques in combating these threats which go way beyond just a firewall and an anti-virus scanner.
Here is a list of the common security protection needed in combating such threats;
- IPS/IDS (Intrusion Prevention/Detection System)
- Zero Day Protection
- DOS and DDOS (Denial of Service and Distributed Denial of Service)
- Application Proxy Filtering on the application layer
- Spam filtering
- URL filtering
- Anti-Phishing
- Anti-spyware
- Rootkit protection
- DLP (Data Leakage Prevention)
- Application control
- NAC
- VPN
The need for so many security features in one box resulted in the terminology UTM appliance. A UTM (Unified Threat Management) appliance is basically a firewall and many other security features all in one appliance. The Watchguard and Fortinet appliances mentioned in my network firewall recommendations are an example of UTM appliances.
UTM appliances are ideal for small to medium sized businesses. Rather than purchasing an anti-spam appliance, URL filter software, Firewall, IPS appliance, etc, they could just opt for an all in one with a UTM appliance which would save them lots of money.
However a larger, enterprise network would benefit more from dedicated appliances. Dedicated appliances give more granularity, control, and more processing power just to concentrate on a particular aspect. For example a company with inbound and outbound mail flow of around 20,0000 a day would require a dedicated SMTP appliance, with a dedicated administrator maintaining the appliance. A UTM appliance would usually not be suitable or capable for this type of mail flow.
Another reason in which a company may decide to purchase dedicated appliances or dedicated software for a particular job, for example a web filter, is because dedicated appliances are always much better equipped and have more powerful rules and granular settings to look after that particular threat. So a web filter program within a UTM firewall will never have as many settings and is as powerful as a dedicated web filter, designed and produced just to look web/url filtering.
Lastly, when using all and every feature a UTM firewall has to offer, this has a massive impact on the UTM firewall’s performance. It is capable of only a small fraction of what it would be capable of if the UTM feature were disabled. This is another reason a company may purchase a dedicated appliance. They may already have a UTM firewall, which is looking after traditional firewall features and VPN, so rather than turning on a UTM feature such as the spam features for example which would have a performance hit on the appliance, they may just purchase a separate anti-spam appliance, looking after their emails for spam and viruses.
An Overview of Firewall Functionality and Types
Firewalls are the forgotten heroes in the Internet of things. Often times users click away on the Internet, completely oblivious to what’s happening behind the scenes. If your firewall doesn’t provide alerts, you may not even know it just stopped malicious code from running on your device.
Protecting your sensitive data from cyber criminals has become increasingly important, and you owe it to yourself to learn a bit about the software that’s protecting you. Read on to learn how firewalls work, why you need them, and how to choose a setup that will best serve your needs.
What Is A Firewall?
To put it in simple terms, a firewall is software that chooses to allow or deny both incoming and outgoing communication through your computer’s ports or local network. Although “hardware” firewalls exist, it’s important to remember that this is just a standalone device running firewall software. Firewalls filter traffic based on a variety of factors, including rules, IP address, connection state, and by referencing databases. Firewalls act as a bouncer, sending away traffic that doesn’t fit criteria.
Firewalls can also be used to filter out places that an administrator doesn’t want a user to go. For example, an admin may block Facebook or YouTube through firewall settings to prevent workers from breaking company policy on Internet usage. They may also filter out sites known to be sources of malware to deter users from accidentally downloading a virus. Firewalls, aren’t a catch all though. For example an e-mail containing a malicious attachment could slip through. Depending on your firewall type, you may be vulnerable to certain attacks.
What Are The Different Types Of Firewalls?
Firewalls protect you in a variety of ways. Network Address Translation and proxy setups can hide your identity from those outside the network, but the main job of a firewall is to filter traffic. Filtration comes in five main firewall types:
Packet Filtering: This is the grandfather of firewalls, and sometimes referred to as a stateless firewall. Packet filters basically inspect a packet, and determine whether or not it fits a rule set that will allow it to pass through the filter. For example, if there’s a rule allowing TCP port 80 traffic inbound/outbound you can communicate using HTTP services. These are cheap, but require a bit of configuration, and they don’t examine entire packets.
Stateful Filtering: This type of firewall still uses packet filtering, but now it also considers the connection state of a device. Initially the firewall inspects packets at the application layer, once a connection is established, the inspection on the application layer is no longer needed. It performs most of its examinations between the Physical and Transport layers of the OSI model. Note that these can be vulnerable to man-in-the-middle attacks (IP spoofing).
Application Layer Firewalls: Application layer firewalls filter by process instead of by port. They are useful in preventing attacks on processes like HTTP and SMTP, guarding against SQL injection, DDoS attacks, and more. These actually filter application level commands and fully inspect the packet. Of course, vendors need to keep pushing out updates for new protocols, and there may be some delay in this support, which could lead to potential exploits.
Circuit Level Gateway: These work on the Session layer of the OSI model to confirm that TCP handshakes between packets are legit. This acts as a circuit for a proxy server and internal clients; and ensures that an external client doesn’t have any actual information about the server. There is potential for harmful information to get through to the proxy to the Internal client because these do not examine packet contents.
Stateful Multilayer Inspection: These are a combination of packet filtering, circuit level gateways, and application layer firewalls. These are fairly complex, and could actually be more insecure than a simple firewall if you don’t have an admin who is knowledgeable about proper configuration.
